Table of Contents
How to map network drives of the Windows central file servers when connected to the VPN?
Documentation from the windows team is here: http://www2.slac.stanford.edu/comp/windows/docs/VPN/VPN.aspx
You can also type in the address bar:
U drive-> \\win.slac.stanford.edu\my_storage\users
V drive -> \\win.slac.stanford.edu\my_storage\groups
Z drive -> \\win.slac.stanford.edu\my_storage\users\$first_letter_winusername\$winusername , for instance if your windows username is jdoe this would be \\win.slac.stanford.edu\my_storage\users\j\jdoe
Why can't I see my network drives (V:, K:, etc.)?
If you are using a SLAC-issued centrally-managed Windows laptop, and you don't see your network drives after connecting to the VPN, you can connect to all these drives by running the script which can be found under \\slac.stanford.edu\netlogon\domainlogon.vbs (type this address into an Explorer window once connected to VPN). It should be possible to create a shortcut or bookmark to this script to make it easier to connect to network drives.
If you are using a personal machine not in the SLAC domain, then domainlogon.vbs does not work. You will need to map your drive manually using http://www2.slac.stanford.edu/comp/net/dialup/faq-dialup.htm#map.
For more information on drive mapping, please see the windows infrastructure page regarding this matter/
What are the timeouts on the VPN connection?
There is a fixed timeout of 12 hours after which your VPN connection is disconnected. There is also a non-activity timeout of 20 minutes which takes effect if no network traffic passes for 20 minutes.
Is there an automatic re-connect feature?
An auto reconnect feature is enabled, but it is only in effect within a session with a duration < session timeout (12 hours). So you can't be connected more than 12 hours without manually re-connecting and re-entering your credentials. This is by design and was explicitly asked by security.
Can I connect to the SLAC VPN using my mobile device, e.g. smartphone?
For the iPhone and iPad running iOS 4.1 or later (multitasking) you need to download the free Cisco AnyConnect client. The iPhone/iPad client is not officially supported, but many users have reported success. This is available from the Apple App Store. For the iPhone app, search the app stores for "Cisco AnyConnect Client". Within the app, select "Add VPN Connection...". Enter vpn.slac.stanford.edu as the server address, this will be replaced with a list of the VPN servers that is automatically updated each time you connect.
There are also Android apps but often they require the phone to be rooted.
SLAC does not provide support for personal devices or such apps at this time, but you are free to make your own attempts to connect using them. Other mobile devices may be able to connect when Cisco releases AnyConnect Secure Mobility clients for those platforms. Any informal support from the OCIO will focus on iOS and Android today and target browsers with HTML5 first
I'm getting periodically disconnected while I work, and I know I wasn't idle for 20 minutes
We have received reports of some users getting disconnected when their wireless signal is not strong. Try moving to a location with a better wireless signal.
Can I Connect to the SLAC VPN From a virtual machine?
Connecting to the SLAC VPN from a virtual machine is not officially supported, but it may work providing the following requirements are satisfied:
- The virtual machine must be configured for "Bridged Networking", as explained by these information pages:
- The operating system on the physical host must not be connected to the SLAC VPN simultaneously
- The virtual machine must be able to access https://vpn.slac.stanford.edu using a browser (to install the client and ensure proper connectivity)
- The virtual machine must be running a compatible version of an operating system which is supported by the Cisco AnyConnect client.
Can I access PeopleSoft?
Yes, you can access PeopleSoft just as you would from your desk while connected to the SLAC VPN.
Can I access internal AFS servers?
Internal AFS servers should be accessible.
In some cases, you will need to renew your Kerberos credentials and establish the connection with the internal AFS servers. Under Mac OS X or Linux,
- on the command line, enter
kinit <username>@SLAC.STANFORD.EDU(where <username> with your SLAC UNIX account name)aklog
This will update your tokens for AFS.
Initial access may incur a delay as the local cache is built.
If you experience an inability to access AFS, please email net-admin@slac.stanford.edu and describe your problem.
Can I access the license server?
The license server may not function well over VPN. There are many failure modes, and most vendors have not upgraded to more recent flexlm versions that are more reliable, nor to support alternative license servers when one fails or needs to be restarted due to upgrades/patching/failure. Also serving a license across a VPN may be a license violation (e.g. if the licenses is limited to a site). At the moment it appears to work, however there are no guarantees.
Can I access SLAC computers using windows terminal services with the new VPN?
You should be able to access SLAC computers via RDP. If not please report this with details as a problem to net-admin@slac.stanford.edu.
Can I access confluence?
You should be able to access Confluence. If not please report this with details as a problem to net-admin@slac.stanford.edu .
Is all network traffic routed through SLAC when connected to VPN? Is traffic logged?
When connected to our VPN service, policy states that all traffic must go through SLAC: Security policies dicate that split tunneling is not allowed.
This also means that all the VPN traffic is going through the same set of security appliances (including webproxy, logging, malicious code checking, spam filters etc.) as those used when you are connecting from SLAC.
After connecting to the VPN, I could not access my local network resources (such as my printer at home)
This is a security feature of the new VPN. Once connected to SLAC, your system is isolated from your local network for your protection. In order to do things like access a home network-shared printer, local network file shares etc., you will need to temporarily disconnect from the SLAC VPN.
After connecting to the VPN, can I print directly to the printer in my office at SLAC?
This is supported for most models of printers. If your particular printer is not accessible, please work with IT Department Support to assess the problem.
I could not ping vpn.slac.stanford.edu
From the internet, you should be able to ping vpn.slac.stanford.edu. However, after you have connected to the VPN servers, you will no longer be able to ping the vpn servers.
In order to test VPN connectivity, you should ping an internal SLAC only server; an example would be www-lanmon.slac.stanford.edu
Are you doing your own testing with a Mac? Or a Windows box?
Testing is being performed with all those, and others, but there are many different OS versions, system configuration options and user use cases. And the SLAC community often has found unique ways of doing things that have simply not been (well) tested.
Any success/failure information adds to the knowledge base. Please submit your experiences at net-admin@slac.stanford.edu
Can I use my mail client with an external provider such as GMail or Apple MobileMe?
Most email providers supply a web-based interface for reading and sending mail, and in most cases those will work through the SLAC VPN.
You may connect to external mail providers from your mail client via IMAP or POP protocols to receive mail, but when using VPN you must send mail through SLAC's authenticated SMTP server (or temporarily shut down the VPN connection)
The SLAC authenticated SMTP server does not look at the From: line, so the email will still appear to be from xxx.xxx@gmail.com. In addition, the SLAC authenticated SMTP server is Internet accessible so you should be able to use it from anywhere.
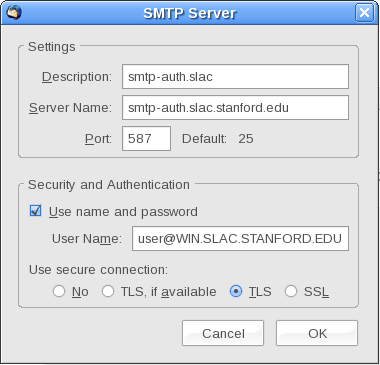
This means (for instance), the outgoing SMTP server in Thunderbird would be set to smtp-auth.slac.stanford.edu, port 587, <Windows/Unix Kerberos principal name>, normal password, STARTTLS.
Please note that most email clients allow you to configure multiple outgoing servers, and will attempt to connect to the default outbound mail server first. If the SLAC server is not the default, you may have to select it when sending mail or wait for the default server connection to time out before mail is sent.
Please see mail-admins page for futher details.
Every time I start a VPN, I have to pick a certificate in below dialog. Any way I can make it default so I don't have to pick?
You can remove certificates using the "Credential Manager":
- Open the Windows menu (formerly the Start menu)
- Type "certmgr.msc" in the Search/Run field at the bottom of the menu
- From the application that launches, delete the certificates in the
"Personal" folder
You may also be able to connect which will load a new client and next time you connect the certificates will not be displayed.
I was disconnected with the message "Administrator Reset", what does this mean and how do I reconnect?
Please ensure you are using the connection string vpn.slac.stanford.edu
It is sometimes required to perform some maintenances on VPN gateways, and this message indicates that the network administrator has disconnected your session so that the VPN server can be rebooted. Thanks to our redundant system, users using vpn.slac.stanford.edu as connection string are not affected by our scheduled maintenances.
If I connect to SLAC's VPN will I lose all my active ssh sessions?
Yes, as all your traffic will be then routed through the VPN tunnel making you appearing from a different IP address to the server. Only persistent connections are affected (ssh, remote desktop...) all other traffic (web surfing,...) will be transparently rerouted through the VPN.
Which login should I use to connect to the new VPN system?
You must use the login of your SLAC windows account, and this account should be enabled for "dialup services".
When putting your login into Cisco anyconnect client's interface please do not prefix it with "SLAC\", only put your login name in the field.
I can't get IPv6 working through the VPN.
IPv6 is currently not enabled for the SLAC VPN and is actively blocked.
Where can I find more information on VPN security issues
See http://csrc.nist.gov/publications/nistpubs/800-113/SP800-113.pdf from NIST.
Can I connect to Stanford university using SLAC VPN?
Yes, Stanford supports the SSL protocol. Instead of connecting to "vpn.slac.stanford.edu", connect to "su-vpn.stanford.edu". You should use your SUNetID and password rather than the SLAC Windows password.
When connected to the SLAC VPN, you can reach Stanford ressources as if you were in your office at SLAC.
Issue connecting to SLAC vpn gateways with Samsung Galaxy devices
1/8/2015: There is an issue with Samsung Galaxy devices having trouble to successfully validate VPN gateways' SSL certificates. When trying to connect to vpn.slac.stanford.edu with the Cisco anyconnect client, or when trying to go with a browser to https://vpn.slac.stanford.edu the device will complain that the certificate is invalid (unknown CA message or alike). Some old systems (Windows XP) may also have similar issue.
This is because on these devices the default keystore is currently missing some intermediate certificates, particularly the one used by thawte to issue SHA-256 certificates (CA issuer name cn=thawte SSL CA - G2).
To have this fixed just go to http://thawte.tbs-certificats.com/thawte_tj.crt with a web browser, it then will ask a name for this certificate. Put something like "Thawte SHA256" and then valid. The cert will be automatically imported in the keystore.
Then if you try to go to https://vpn.slac.stanford.edu or if you try to connect to the SLAC VPN gateways with the cisco anyconnect client it will work without issuing a warning.