There are a number of desired and required features that are not provided by the Windows VPN servers. Some of those features include:
If you are using a SLAC-issued centrally-managed Windows laptop, and you don't see your network drives after connecting to the VPN, you can connect to all these drives by running this script: \\slac\netlogon\domainlogon.vbs. It should be possible to create a shortcut or bookmark to this script to make it easier to connect to network drives.
There is a fixed timeout of 8 hours after which your VPN connection is disconnected. There is also a non-activity timeout of 20 minutes which takes effect if no network traffic passes for 20 minutes. If you have a legitimate requirement for a VPN connection which is not subject to these timeouts, please contact account-services@slac.stanford.edu to request an exception. Your VPN will also be disconnected if your system goes to sleep. IT Department Support can assist you if you need to adjust the sleep settings of your system, they can be contacted at ithelp@slac.stanford.edu .
There is an app for the iPhone and iPad which some users have had success with. There are also Android apps but often they require the phone to be rooted. SLAC does not provide support for personal devices or such apps at this time, but you are free to make your own attempts to connect using them. For the iPhone app, search the app stores for "Cisco AnyConnect Client". Within the app, select "Add VPN Connection...". Enter vpn.slac.stanford.edu as the server address, this will be replaced with a list of the VPN servers that is automatically updated each time you connect. Other mobile devices may be able to connect when Cisco releases AnyConnect Secure Mobility clients for those platforms.
We have received reports of some users getting disconnected when their wireless signal is not strong. Try moving to a location with a better wireless signal.
Yes, please follow the instructions on this page:
Connecting to SLAC's VPN Using Mac OS X
Yes, please follow these instructions:
Connecting to SLAC's VPN Using Linux
For the iPhone and iPad running iOS 4.1 or later (multitasking) you need to download the free Cisco AnyConnect client. This is available from the Apple App Store. Enter the server as vpn.slac.stanford.edu. The iPhone/iPad client is not officially supported, but many users have reported success.
Connecting to the SLAC VPN from a virtual machine is not officially supported, but it may work providing the following requirements are satisfied:
Yes, you can access PeopleSoft just as you would from your desk while connected to the SLAC VPN.
Internal AFS servers should be accessible. In some cases, you will need to renew your Kerberos credentials and establish the connection with the internal AFS servers. Under Mac OS X or Linux, you can enter at the command line "kinit <username>@SLAC.STANFORD.EDU" to renew your Kerberos credentials (replace <username> with your SLAC UNIX account name, and make sure the domain is all upper-case, as shown here), folowed by the command "aklog" to connect to the AFS infrastructure. Initial access may incur a delay as the local cache is built. If you experience an inability to access AFS, please email net-admin@slac.stanford.edu and describe your problem.
The license server may not function well over VPN. There are many failure modes, and most vendors have not upgraded to more recent flexlm versions that are more reliable, nor to support alternative license servers when one fails or needs to be restarted due to upgrades/patching/failure. Also serving a license across a VPN may be a license violation (e.g. if the licenses is limited to a site). At the moment it appears to work, however there are no guarantees.
You should be able to access SLAC computers via RDP. If not please report this with details as a problem to net-admin@slac.stanford.edu .
You should be able to access Confluence. If not please report this with details as a problem to net-admin@slac.stanford.edu .
When connected to our VPN service, policy states that all traffic will go through SLAC. We do not use split tunneling.
This is a security feature of the new VPN. Once connected to SLAC, your system is isolated from your local network for your protection. In order to do things like access a home network-shared printer, local network file shares etc., you will need to temporarily disconnect from the SLAC VPN.
This is supported for most models of printers. If your particular printer is not accessible, please work with IT Department Support to assess the problem.
From the internet, you should be able to ping vpn.slac.stanford.edu. However, after you have connected to the VPN servers, you will no longer be able to ping the vpn servers.
In order to test VPN connectivity, you should ping an internal SLAC only server; an example would be www-lanmon.slac.stanford.edu
Regardless of getting VPN to work, note that Apple is about to release Lion (10.7), and will likely drop support for 10.5 (while they have not stated that officially, that has always been the way Apple does things; two versions are supported, otherwise you need to upgrade). And, as you know, the PPC/G5 is not supported in 10.6/10.7, so you really need to plan to replace that system. When Apple releases security fixes for 10.6/10.7 and not for 10.5 (figure August-ish, but that is a WAG), 10.5 will no longer be in compliance to connect to the internal SLAC network.
The Cisco AnyConnect client for PPC is stuck at version 2.5. Although Cisco has been releasing security patches for that version, it is one major release behind the current software for all other platforms, which is at 3.0.
We performed significant testing of the 2.5 client, including on PPC systems, but eventually we made the decision to support only 3.0+ client versions due to the small number of users who would be affected, and the assumption that Apple will not continue to support PPC systems with OS updates for very long (we don't know for sure, but are making an educated guess based on Apple's past behavior).
Testing is being performed with all those, and others, but there are many different OS versions, system configuration options and user use cases. And the SLAC community often has found individual ways of doing things that have simply not been (well) tested.
Any success/failure information adds to the knowledge base.
Most email providers supply a web-based interface for reading and sending mail, and in most cases those will work through the SLAC VPN.
You may connect to external mail providers from your mail client via IMAP or POP protocols to receive mail, but when using VPN you must send mail through our authenticated SMTP server (or temporarily shut down the VPN connection). The SLAC authenticated SMTP server does not look at the From: line, so the email will still appear to be from xxx.xxx@gmail.com ... and the SLAC server is Internet accessible so you should be able to use it from anywhere.
This means (for instance), the outgoing SMTP server in Thunderbird would be set to smtp-auth.slac.stanford.edu, port 587, <Windows/Unix Kerberos principal name>, normal password, STARTTLS.
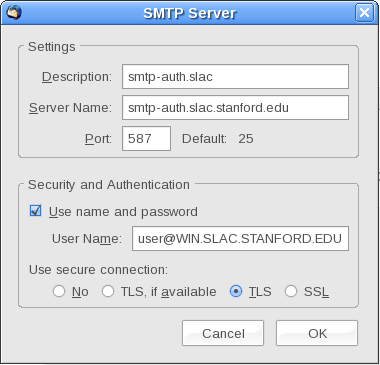
Please note that most email clients allow you to configure multiple outgoing servers, and will attempt to connect to the default outbound mail server first. If the SLAC server is not the default, you may have to select it when sending mail or wait for the default server connection to time out before mail is sent.
You can remove certificates using the "Credential Manager":
You may also be able to connect which will load a new client and next time you connect the certificates will not be displayed.
It is occasionally necessary to reboot the VPN servers in order to install patched software, or to enable new features. This message indicates that the network administrator has disconnected your session so that the VPN server can be rebooted. Click "OK" when you receive this message, and you should be able to connect again after approximately 1 minute. If you want to reconnect immediately, select an alternate server name from the AnyConnect connection window before reconnecting (e.g. change fwvpn1.slac.stanford.edu to fwvpn2.slac.stanford.edu).
Yes, as all your traffic will be then routed through the VPN tunnel making you appearing from a different IP address to the server.
Only persistent connections are affected (ssh, remote desktop...) all other traffic (web surfing,...) will be transparently rerouted through the VPN.
You must use the login of your SLAC window account, and this account should be enabled for "dialup services".
When putting your login into Cisco anyconnect client's interface please do not prefix it with "SLAC\", only put your login name in the field.