...
Many users are familiar with SSL encrypted web pages that ask them for their username and password to log into a web sitelogin to web sites. With SSL, web browsers use a gold lock as a visual cue to indicate to users that their username and password will be transmitted securely over the Internet. For example, this is what Wells Fargo Bank customers see in the lower right hand corner of the Internet Explorer 6.0 and FireFox 1.0 browsers when they log into their account:
...
Although SSL is widely used to allow users to securely log into a web sitelogin to web sites, it is not the only method that modern browsers support. Another method, which is just as seccureat least as secure as SSL (if not more so), is called Interated Windows Authentication (hereafter called IWA). Most web browsers (all versions of Internet Explorer, and recent versions of Gecko-based browsers such as FireFox 1.0) support IWA. In some ways IWA is more secure than SSL since IWA never sends the username and password to the remote web server. Although SSL sends the username and password in an encypted format, once it arrives at the web server it is in clear-text and could be accidently exposed by an inexperienced web programmer. IWA does not suffer from this vulnerability since the username and password never leave the browser.
Whereas SSL uses the widely recognized gold lock visual cue to indicate to the user it is safe to type your password, IWA uses a different (but just as valid) visual cue to reassure the user it is safe to type your password. Some users have recently raised the concern that since the Since the visual cues are different for the SSL and IWA methods, that some reassureance of the safety and validity of IWA be given is being provided to the GLAST community , which is in the purpose form of thie this article.
How IWA works
Roughly speakigspeaking, there are two ways to authenticate a user to a web site called Forms Based Authentication and Browser Based Authentication. The method many users are familiar with is Forms Based Authentication, which is when a form embeded in a web page prompts a user for their username and password over an SSL connection to the web server. The user types their username and password into the web form and clicks the submit button which sends the credentials to the web server over the encypted SSL channel for authentication. It is important to point out that the user's web browser has no idea that the user is logging into the web site - all that the web browser knows is that it is sending information to the remote web site over an SSL channel.
...
Back at the browser, the browser attempts to decrypt the challenge with the user's password to get the answer to the challenge, which the browser then sends to the web server as proof that the user is who they claim to be. If the web server determines that In the diagram below, the string of characters after the line Authorization: NTLM is what the browser thinks the answer is correct, the web server sends the originally requested page . In this case, the user provided valid SLAC credentials to the browser. If not, and the user is presented with a "Unauthorized Access" page:
If the User Provides the Wrong Password |
|---|
original page is served:
| Panel | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||
http://glast-ground.slac.stanford.edu/ GET / HTTP/1.1 HTTP/1.x 200 OK |
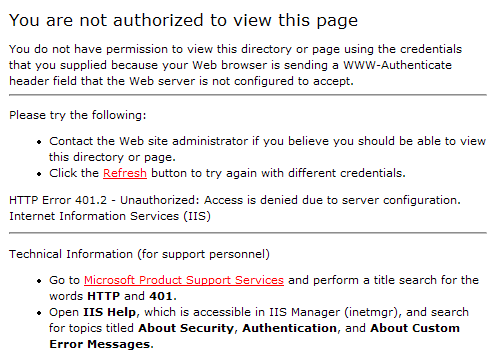
If the web server determines that the answer is correct, the web server sends the originally requested page to the browser. If not, the user is presented with a "Unauthorized Access" page. For example, if I given the wrong username and/or password, the user will see the following page.
If the User Provides the Wrong Password |
|---|
Conclusion
IWA is a valid and secure way for web sites to authenticate users over insecure networks such as the internet. The username and password are never sent in clear-text over the internet. It is just as secure as SSL, and uses visual cues to indicate to the user who is requesting their credentials. If the user trusts the web site, then they can feel comfortable submitting their credentials to it.
For GLAST users, since SCS has vetted the web site http://glast-ground.slac.stanford.edu/, they can trust that security is implemented properly and should feel secure in using it.