...
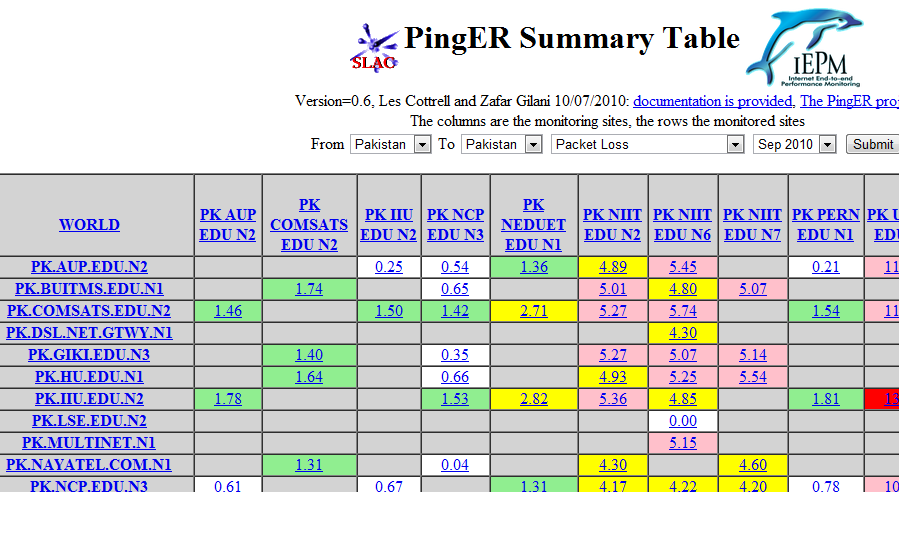
The script table.pl takes PingER data and provides a table for various network performance metrics (such as RTTs, Packet Loss, Throughput, etc) from monitored to monitoring hosts in a simple but color-coded fashion (documentation available here). The script was originally written by Dr. Les Cottrell. Later Zafar Gilani modified it. The script now conforms to perl warnings and tainting mode. New version is now installed both at SLAC and SEECS.
...
Tainting on the other hand is used to make sure that a CGI script is logically secure. Taint (T) mode puts a Perl script into paranoid mode and treats all user supplied input as tainted and bad unless the programmer explicitly OKs the data. Read more here.
To display warnings (w) and enable tainting (T), add the following line at the top of the script:
| Code Block |
|---|
#!/usr/bin/perl -wTw |
The above is pretty much an older style of Perl coding. One can also use:
| Code Block |
|---|
..
use warnings;
..
|
To enable tainting (T), just add the letter 'T' at the end of the top line of a script:
| Code Block |
|---|
#!/usr/bin/perl -wT
|
Once tainting is enabled, it has to be used at the command prompt as well or the script won't run. If one tried to run the script without tainting option (-T) from command line, the script fails with following message:
...
Don't enable all the options above in one go. There will be a humongous number of warnings and error messages. The best way to do this is tediousto go stepwise. Enable the above options one by one, in the order written above one by one:below. This must be followed by test running the script:
- strict
- warnings (enabled diagnostics as required)
- tainting
Once one of the options are enabled, run the program and entertain the warnings and solve error messages. This shall be repeated until all the messages are resolved for that particular step. Also test the html output of the script by saving and accessing the html script via a web browser. A correct output looks something like below:
Deploy @ SEECS
Once finished, deploying at SEECS is trivial given you have root access to the pinger machine. I deployed script at the following path on pinger.seecs.edu.pk
| Code Block |
|---|
/var/www/cgi-bin/table.pl
|
A couple of pre-requisite configuration files that are mentioned inside the table.pl script are placed at the following paths at pinger.seecs.edu.pk:
| Code Block |
|---|
/var/www/html/pinger.new.cf
/var/www/html/nodes.cf
|
Once copied and paths changed, change file access permissions and ownership of table.pl
| Code Block |
|---|
chmod 755 table.pl
chown pinger:pinger table.pl
|