...
- 1965: Larry Roberts and Thomas Marill create the first wide area connection via telephone line, turns out to be inefficient and costly. Kelinrock Kleinrock predicts that packet switching (developed by Baran, Davies, Kleinrock et. al. is more promising)
- 1969 the original Internet created and had 4 nodes, UCLA, Stanford Research Institute, MIT, Utah, 50kbit backbone (today a modem nb scaling up a million times) Jan 83 400 nodes, now 750M
- Built as a collaboration of global proportions, independent stand on own, self managed autonomous systems (Bill Cheswick autonomous map 1999) , decentralized (chaotic, no central control/management cf phone system), best effort, no guarantees, recovery from losses, pipelining (TCP), host flow control, checksums, non-proprietary (c.f. SNA, DECnet, XNS …), little focus on security (if had focused on this might never have happened), simple black boxes (routers connect nets) that do not retain information about the individual flows, packets inside envelopes, layering (independent of each other, i.e. middle layers don’t know if lower layers are wireless, satellite, copper, fibre, upper layer independent of applications cf purpose designed TV broadcast networks, cable networks, telephone network, only end device knows what the contents mean).
...
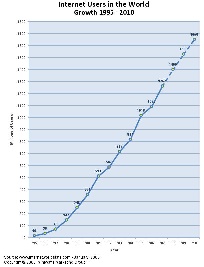
- Growth in usage in last decade, see http://news.bbc.co.uk/2/hi/technology/8552410.stm
- CPUs early 60’s ~ 50 years ago Stretch 1.2MIPS, $8M, today 3GHz $150, i.e. 3000 times faster 50,000 times cheaper,
- WANs 1960s 75bps modems, now 10-100Gbps, i.e. billion times faster (see http://www.ziplink.net/users/lroberts/IEEEGrowthTrends/IEEEComputer12-99.htm)
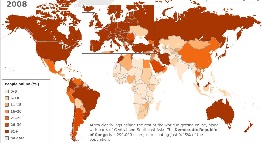
1.6B users visible in 2010, large number hiding behind FW, current usage largest group in China and still small % penetration (tells where products go), 75% of world still to connect, mobiles big help when in research domain)
Problems:
- Address space IPv6 (IPV4 only an experiment so 32 bits were fine, but went into production)
- DNS has vulnerabilities so need digital signatures to prevent poisoning and directing traffic where it does not belong (DNSSEC)
- Security: Spam, viruses, Trojan horses, DOS, DDOS, mistakes of routing, weak OS, naïve browsers and users, (not everyone in the general public has everyone else’s best interests in mind, initial trust
- Mobility (used to be to connect big computers that do not move around, now as move around need to change IP address), persistence, presence, more than best effort (QoS), mesh & sensor nets, delay and disruption tolerance (Internet does not do well in these cases), allow device to move with different IP addresses (today looks like a hi-jack so need to have mechanisms to establish trust between parties if allow dynamics), also in mobile world the topology changes(TCP/IP OK for links going up and down) not well solved, persistent connections do not exists since no session layer so hard to re-establish a session at the place where it left off, self-organised nodes discover each other but bad guy may join how does one stop this, how does one trust the others – e.g. military if post over-run and bad guy gets device she can join, how to stop it.
- Security
- spam, malware, worms, trojan horses ...,
- basic system has no authentication, authorization, accounting
- Lack of tools for strong authentication and identification are needed for some applications (e.g. safe to use the cloud)
- organized crime, state sponsored intelligence gathering, privacy.
- Freedom of information vs privacy, wikileak, elections, riots, how much information is say Google gathering about you (every email if use gmail is saved, search information etc.)
http://www.googlesharing.net/They know who your friends are, where you live, where you work, and where you spend your free time. They know about your health, your love life, and your political leanings. These days they are even branching out into collecting your realtime GPS location and your DNS lookups. In short, not only do they know a lot about what you're doing, they also have significant insight into what you're thinking. see http://www.googlesharing.net/
- performance at first just getting it to work was a major challenge, now time to think of how to improve performance and it is difficult to create a new network. Think back to start of Internet, at the time there was a functioning worldwide network = the telephone net so how could another one take over, but it did.
- Address devices inside an end point
- Broadcast turned into unicast, Multicast could be more efficient for some apps
...